Let’s understand first what is computer network then we will discuss the components of computer network, so let’s start.
What is Computer Network?
- A computer network is a collection of interconnected devices, such as computers, servers, and storage devices, that are connected together to share resources and exchange information.
- A computer network is made up of various components that work together to provide communication and data exchange between devices on the network.
- Networks allow devices to communicate and share data, resources, and applications, providing users with increased functionality and convenience.
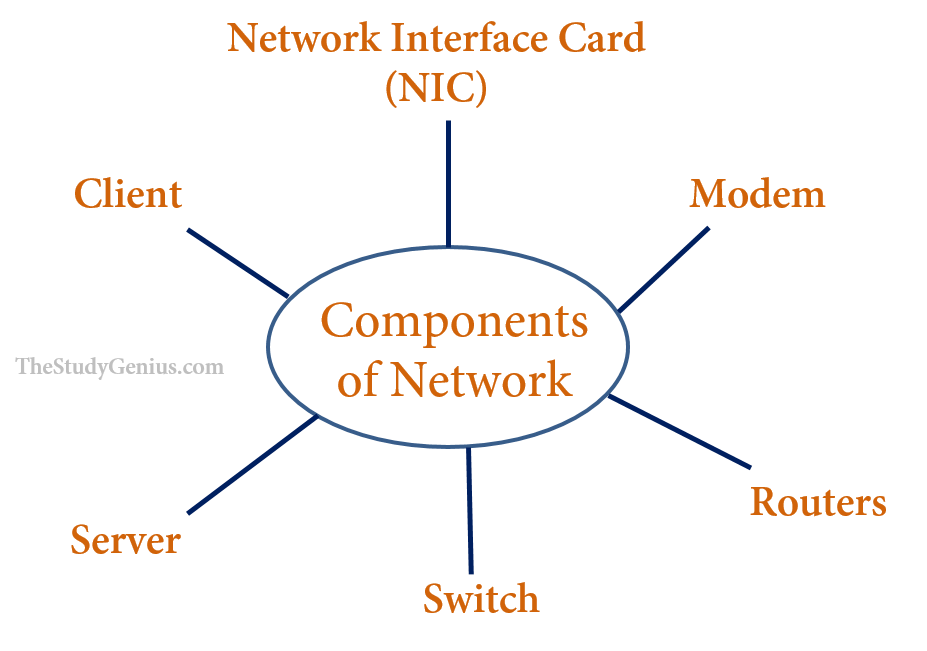
Computer Network Components are:
Table of Contents
HUB
- A hub is a networking device that is used to connect multiple devices or segments on a local network.
- It is not an intelligent device because it does not have any memory to store device information.
- If a computer wants to send information to another computer, the hub broadcasts information to all the other computers, connected to the hub, that’s why it is not an intelligent device.
You should also read: How Hub works? or HUB Vs Switch

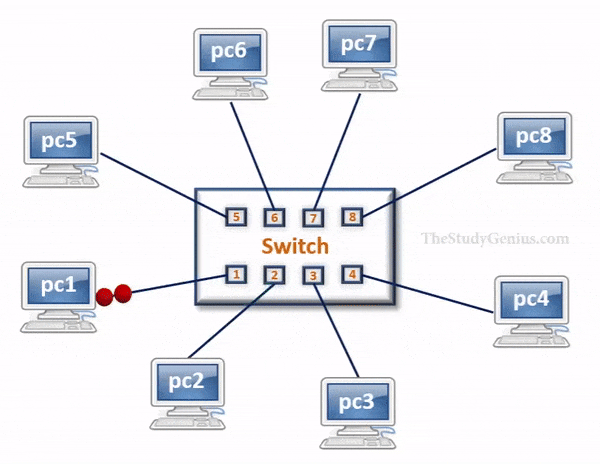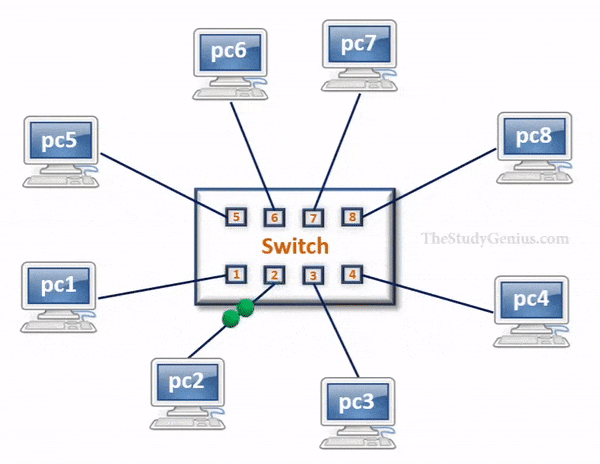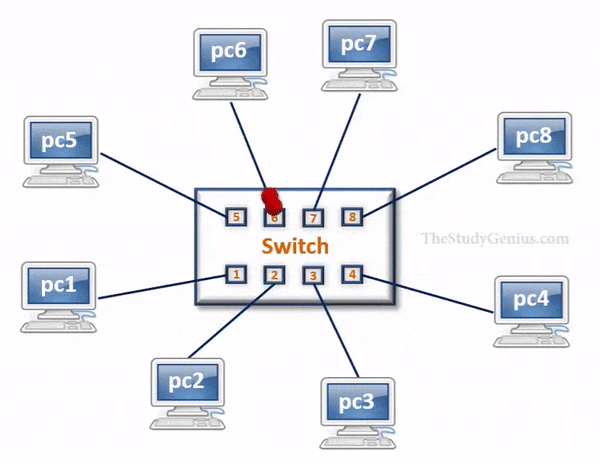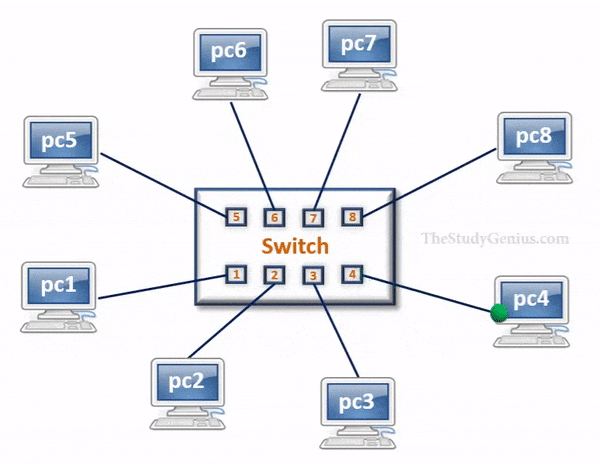
Switch
- Switch is a network device that has multiple ports that are used to connect devices and create a network.
- It is called a Layer-2 device because it forward frames based on MAC addresses.
- It has storage capability, where a table is maintained that helps to identify every device connected to the switch on the basis of MAC addresses.
You should also read: How Switch works?
Routers
- A router is a device that is used to connect multiple networks together.
- It is an internetworking device that receives data packets from one network and forwards it to another network.
- It operates at the network layer (layer-3) of the OSI model and is used to route data between different networks.
- Routers can be used to connect a local area network (LAN) to a wide area network (WAN) or to connect multiple LANs together.
- It allows us to connect to the internet, which is a group of multiple networks.
- It is the only device, which can forward packets from one network to another network.
You should also read: How Router works?
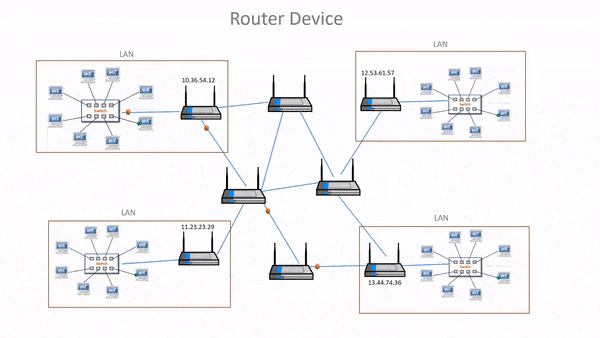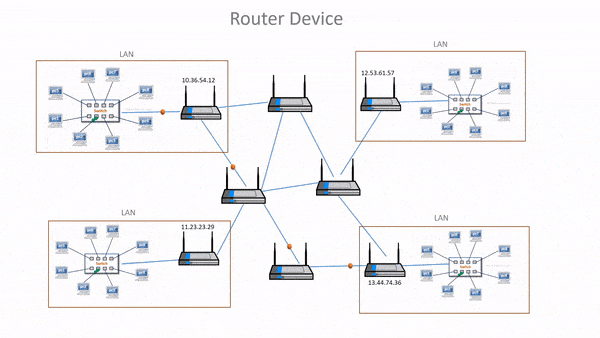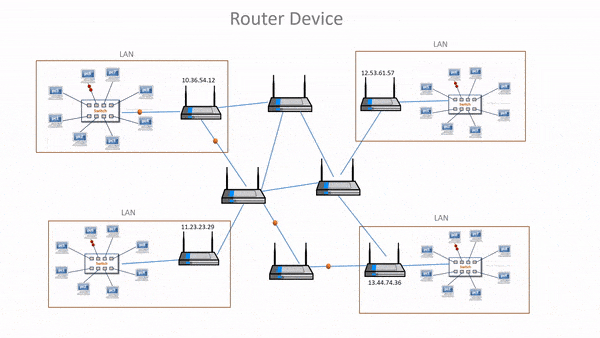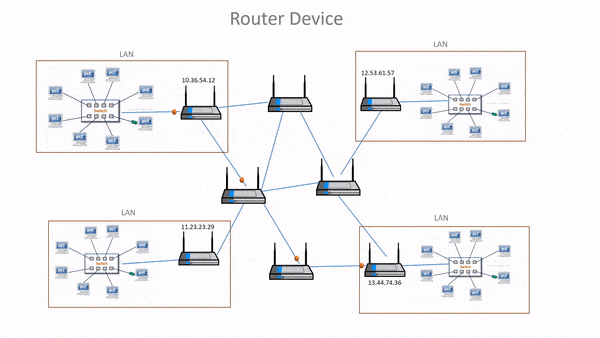
- Routers manage routing table that stores routes of various nodes in a computer network.
- Routing table is a list of routes stores in a router.
- When data needs to be sent from one node to another on the network, then the routing table is referred to in order to find the best possible route.
Read this: What is a routing table? or Router Vs Switch
Modem
- A modem is a device that is used to connect a computer to the Internet.
- It operates at the physical layer of the OSI model and is used to convert digital signals from a computer into analog signals that can be transmitted over a telephone line.
- It works as a signal translator because it translates one signal to another signal so the computers and telephone lines can interact with each other.
- Modems can be external or internal and can be used to connect to the Internet using dial-up or broadband services.
- It is also known as a modulator-demodulator.
MO + DEM= Modulator, Demodulator
It’s used modulator and demodulator to modulate and demodulate the sine wave for encoding and decoding digital information for sending and receiving data.
Also Read: Why do we use a modem?
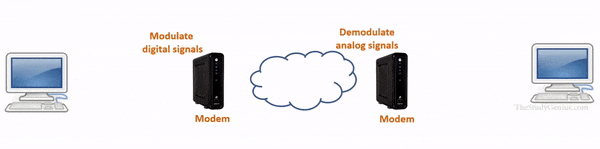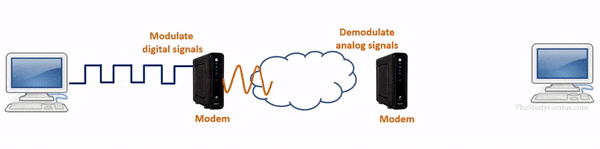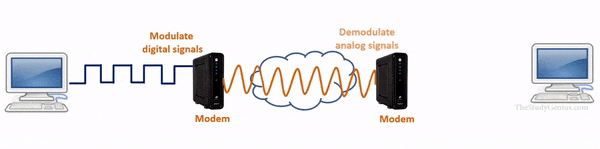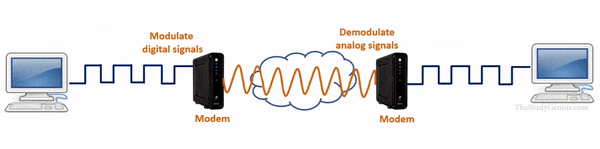
Actually, there is two type’s of signal one is analog signals and digital signals.
A computer only reads digital signals while on the internet analog signals are used. So modulator and demodulator are used where modulator converts computer’s digital signals into analog signals so data can be sent on internet and demodulator convert incoming analog signals from the internet into digital signals so that a computer can understand it.
You should also read: How Modem works?
Network Interface Card (NIC)
- NIC is a network component that is used to connect devices from the network.
- It works on the physical layer and the data-link layer and is responsible to exchange the computer’s data with a network.
- NIC collects the data from the computer and sends it to the transmission Channel.
- For example: If I have a computer and I want to connect with other computers, I need a NIC card to connect the network.
- Another Example, If I have a company where have 100’s of computers and I want to create a local network in my company then I need a NIC card on every computer or laptop so all computers can connect to each other.
- Network Interface cards may be used for both wired and wireless connections.
- Every NIC card contains a unique MAC address that can never change because the address is assigned at the factory where NIC is manufactured.

You should also read: How NIC works?
Channels
Channels are the medium that is used to transfer the data from one place to another place. It is used to carry data from the transmitter to the receiver. It is a path over which information travels between clients and servers in the network. Channels are the transmission media which selected on the basis of their speed and capabilities.
Firewall
- A firewall is a security device that is used to protect a network from unauthorized access.
- It operates at the network layer of the OSI model and is used to block unauthorized access to a network.
- A firewall can be hardware-based or software-based and is designed to control the flow of network traffic by allowing or denying access based on predefined security rules.
- Firewalls are typically configured to block incoming traffic from the Internet and to allow outgoing traffic from the network. This helps to prevent unauthorized access to the network and to protect sensitive information from being compromised.
- Firewalls can also be configured to block specific types of traffic, such as email or file sharing, based on the type of traffic and the source and destination of the traffic.
Access Point
- An access point (AP) is a device that is used to provide wireless connectivity to a computer network.
- It operates at the data link layer of the OSI model and is used to extend the range of a wireless network.
- Access points can be used to connect wireless devices such as smartphones, tablets, and laptops to a wired network.
- Access points use a radio frequency (RF) signal to communicate with wireless devices and can support multiple devices at the same time.
- Access points can be configured with different security options, such as WEP (Wired Equivalent Privacy), WPA (Wi-Fi Protected Access), or WPA2 (Wi-Fi Protected Access 2) to provide security for the wireless network.
- They can also be configured with different wireless standards, such as 802.11b, 802.11g, or 802.11n, to support different types of wireless devices.
Client
- A client is a program or a computer that runs on the local machine and requests from the server computer for services on a network. Client sent the request and receive data from the server.
- Actually, the client machine provides an interface to a user to request services from the server machine, and the server machine responds to the client’s request to give the result.
- A client can be a simple program or a whole computer that requests services from the server.

Server
- A Server is a powerful computer machine, which provides some services to its clients.
- When a computer shares its resources with client machines, they are called servers.
- Server shares our resources with their client’s users.
- They can handle many clients at a time.
- These are also called host computers.
- These are the powerful machines, wait for the request to arrive from clients and then respond to them.
There are many different types of servers:
- File servers
- Print servers
- Application Servers
- DNS Servers
- Mail Servers
- Web Servers
- Database Servers
- Virtual Servers
- Proxy Servers
Virtual Private Network (VPN)
- A Virtual Private Network (VPN) is a technology used to securely connect a device to a network over the Internet.
- It creates a private network connection between the device and the network, allowing users to access network resources as if they were directly connected to the network.
- VPNs are used to provide secure and remote access to a network and to protect sensitive data from being intercepted during transmission.
Network Attached Storage (NAS)
- Network Attached Storage (NAS) is a type of storage device that is designed to provide centralized data storage for a computer network.
- It is connected to the network and is accessible by multiple devices on the network, allowing users to share files and access data from any device on the network.
- A NAS device typically contains one or more hard drives and has its own built-in operating system that manages the storage and retrieval of data.
- NAS devices can be managed through a web-based interface and can be configured with various security options to protect the data stored on the device.
- NAS devices are used for many different purposes, including file sharing, backup and recovery, and data storage.
- They provide a convenient and flexible way for users to store and access data on a network, without having to rely on a dedicated server or computer.
- NAS devices can be used in a variety of environments, including small and medium-sized businesses, home networks, and large enterprises.
- They can be connected to a network using a wired or wireless connection and can be configured with various storage options, such as RAID (Redundant Array of Inexpensive Disks) to provide data protection and availability.